Hacktober CTF is an event that organized by Cyber Hacktics. I participated with @batcain and @hackerbecker as Numinious Episcopate. We solved 51 challenges in SQL, Programming, Steganography, Cryptography, OSINT, Forensics, Traffic Analysis, Linux and Web Exploitation categories. I’ll be showing some of them right now. You can find other challenges at hackerbecker’s github.
SQL
Past Demons
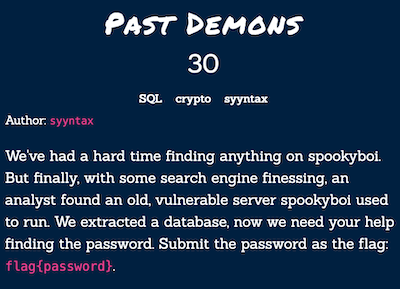
We have a sql file out.db. When I see the file type in terminal it was SQLite 3.x database. So I opened it with sqlite3.
As we see there are some passwords belongs to users. spookyboi’s id is 8. I searched 59dea36d05aacaa547de42e9956678e7 on google and find some hash-password list on github. There it is our spookyboi’s password.
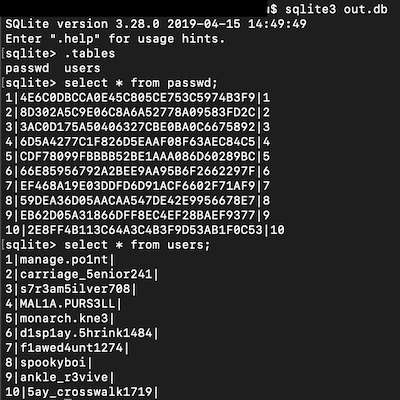
59dea36d05aacaa547de42e9956678e7:zxcvbnm
It is MD5 hash, so you can decrypt it online to find the password.
flag{zxcvbnm}
Address Book
I just opened the sql file with text editor and search for the luciafer. I got lucky with lucia. There was a user LUCIA and her email address.
luc1afer.h4vr0n@shallowgraveu.com
We can follow different way for this and further related SQL challenges. We can create our local database with given sql file. First conntect to mysql and create database.
$ mysql -uroot -p
CREATE DATABASE westridge;
USE westridge;
Then from another terminal, import sql file to database you create. In my case its westridge.
$ mysql -uroot -p westridge < /path_to_file/shallowgraveu.sql
Now search for email like ‘luc’ from users table.
SELECT * FROM users WHERE email LIKE '%luc%';
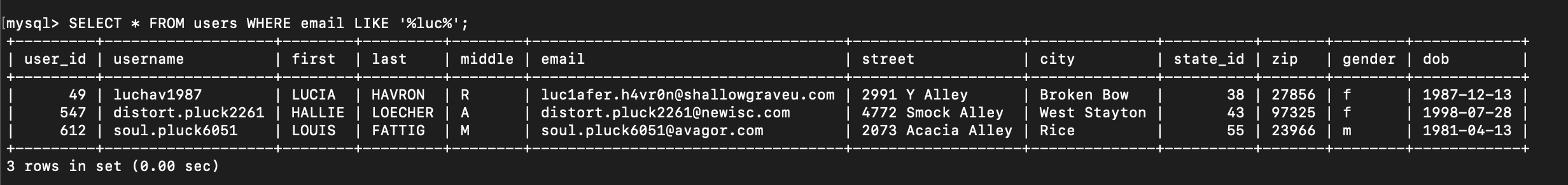
flag{luc1afer.h4vr0n@shallowgraveu.com}
Null and Void
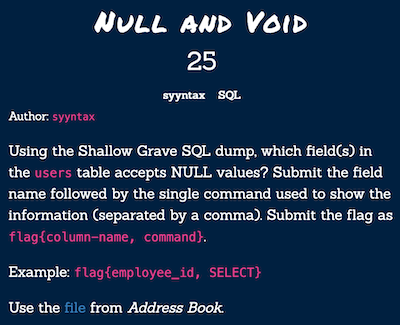
We need to find the field accepts NULL values and command to show the information. Quickly I look at the create table description in the sql file. middle column has DEFAULT NULL attribute. For command first I tried SELECT but it wasn’t the right choice, so I tried SHOW instead.
Another way is to show in terminal.
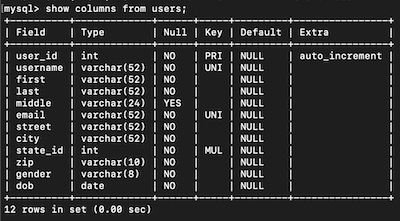
flag{middle, SHOW}
Body Count
We need to count users in Shallow Grave University.
SELECT COUNT(*) FROM users;
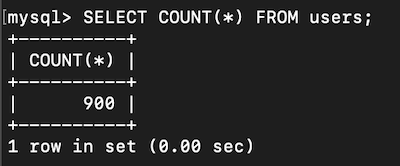
flag{900}
Calisota
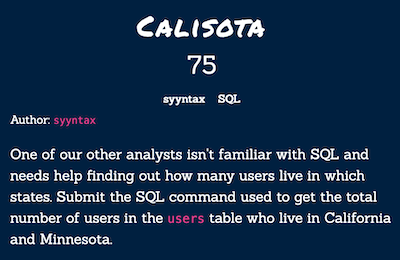
We need to find California and Minnesota state_id’s and count users.
SELECT * FROM states WHERE state_full="California" OR state_full="Minnesota";
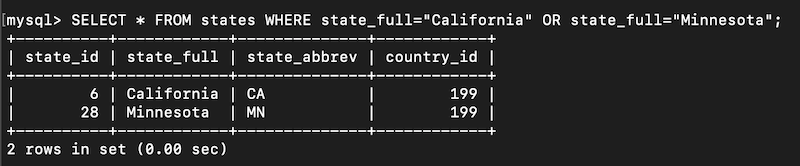
SELECT COUNT(*) FROM users WHERE state_id=6 OR state_id=28;
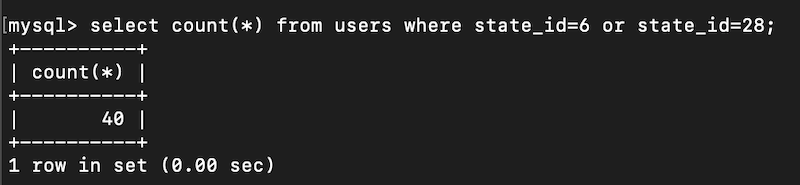
flag{select count(*) from users where state_id=6 or state_id=28;}
90s Kid
Here is the query for number of kids in born October 90s.
SELECT COUNT(*) FROM users WHERE dob LIKE '199%-10-%';
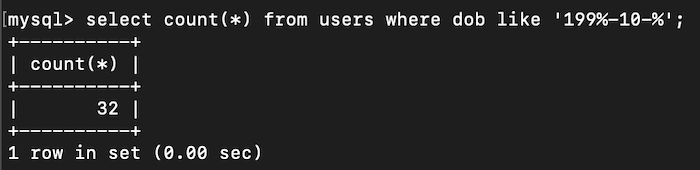
flag{32}
Jigsaw
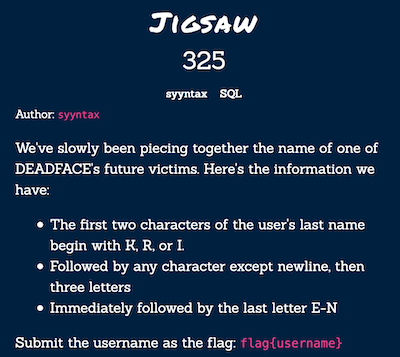
I wrote regex that satisfies the requirements.
SELECT * FROM users WHERE last REGEXP '^[KRI][KRI]....[E-N]$';
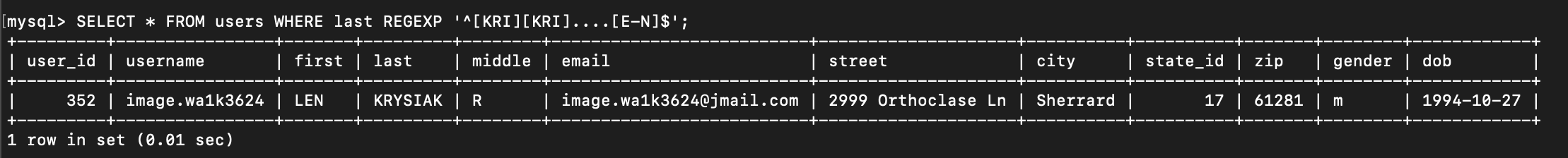
Here is the user which last name is KRYSIAK.
flag{image.wa1k3624}
Programming
Red Rum
We need to connect to nc service and send the Red Rum output. Here is my c++ function.
#include <iostream>
using namespace std;
int main(int argc, const char * argv[]) {
string arr[500];
for (int i=1; i<=500; i++) {
if (i % 3 == 0) {
if ( i % 5 == 0) {
cout << "RedRum,";
}else{
cout << "Red,";
}
}else if(i % 5 == 0){
cout << "Rum,";
}else{
cout << i << ",";
}
}
}
But if you want python, here it is.
for i in range(1,501):
if i % 3 == 0 and i % 5 == 0:
print('RedRum,', end='')
elif i % 3 == 0:
print('Red,', end='')
elif i % 5 == 0:
print('Rum,', end='')
else:
s = str(i)+','
print(s, end='')
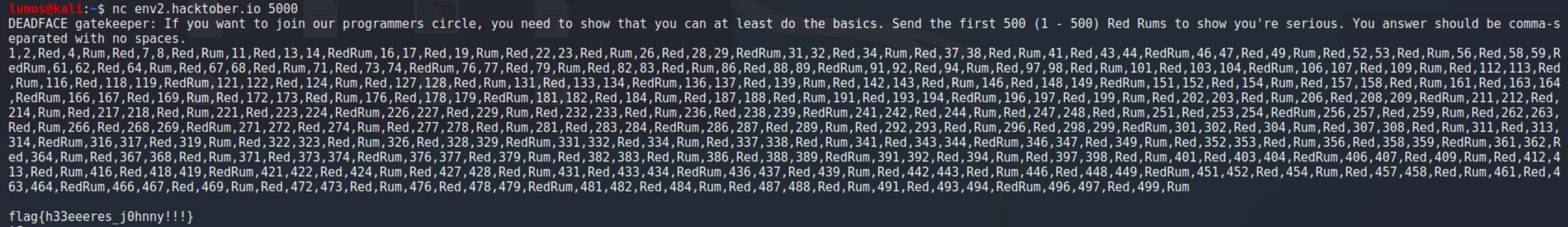
flag{h33eeeres_j0hnny!!!}
Stairway To Hell
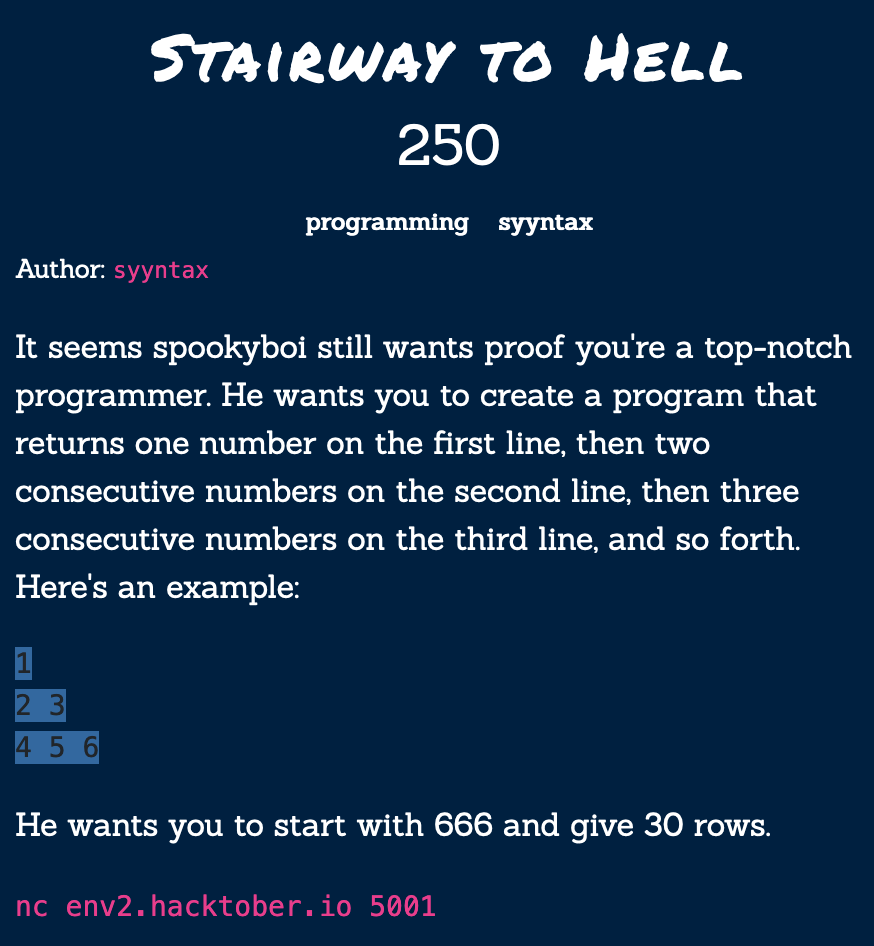
Write code to build a staircase but put it in one line -__-
#include <iostream>
using namespace std;
int main(int argc, const char * argv[]) {
int num = 666;
int j= 0;
for (int i=0; i<30; i++) {
for (j=0; j<i+1; j++) {
cout << num + j << " ";
}
num = num + j;
}
return 0;
}
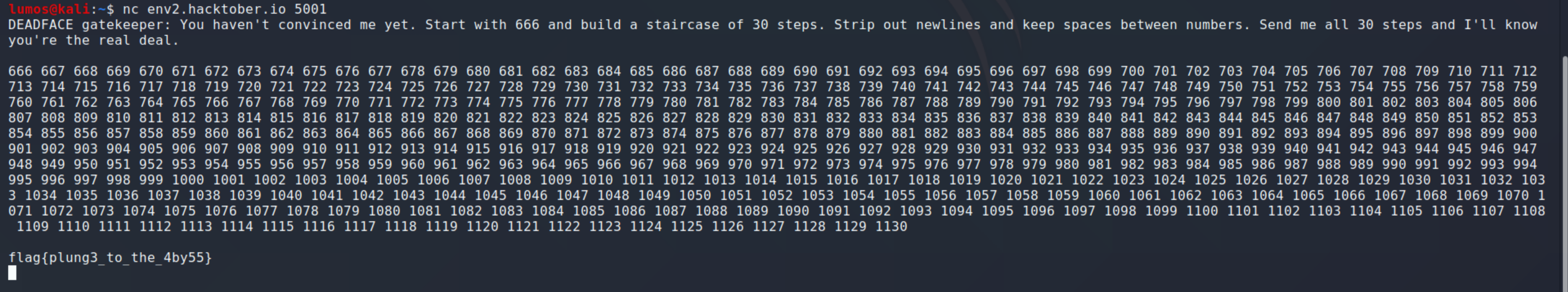
flag{plung3_to_the_4by55}
Password Check
Actually I didn’t do anything about programming in this challenge. I just use hashcat and used haveibeenpwned site for find how many times this password compromised. Download the hash list and give it to hashcat as input.
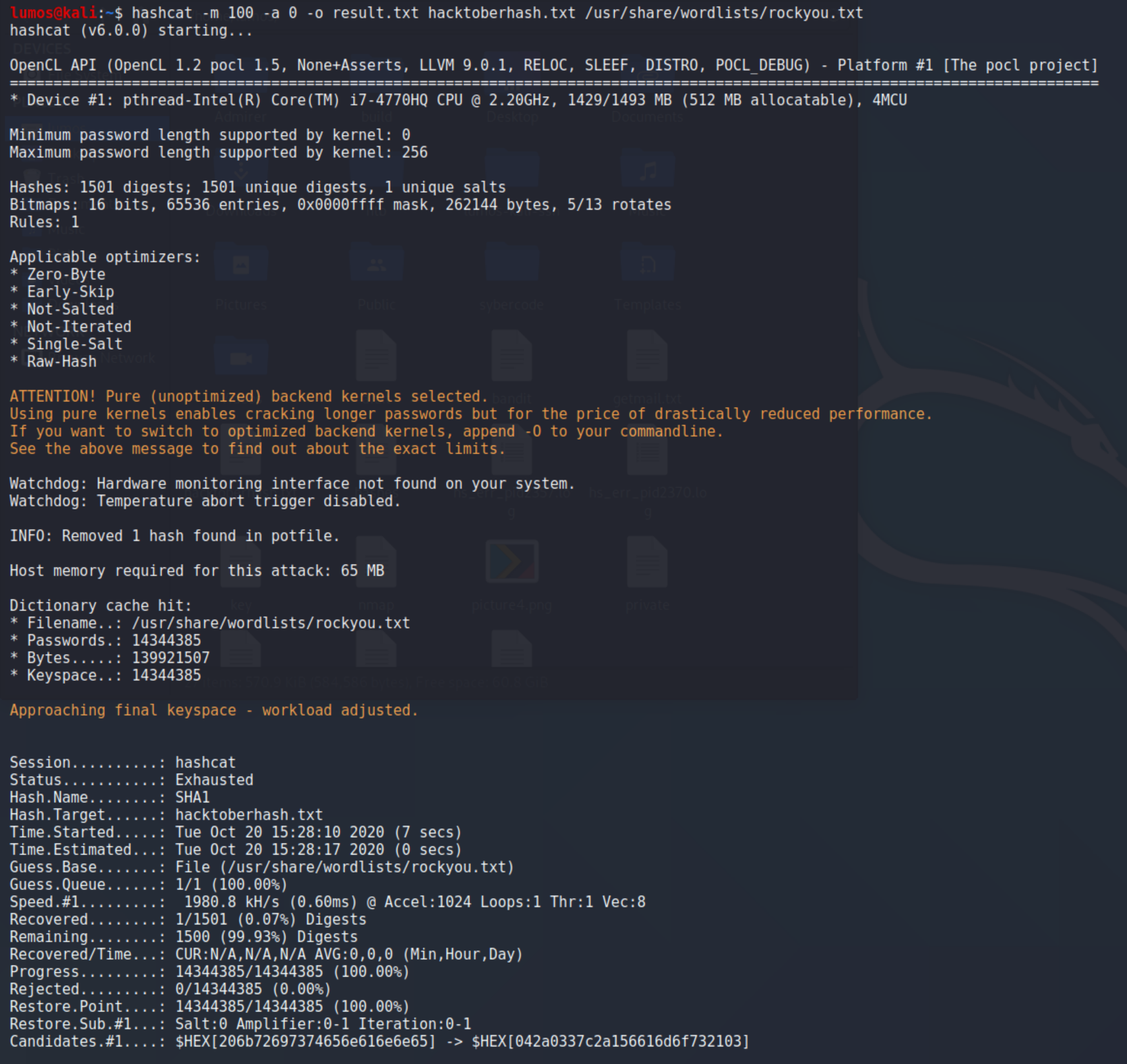
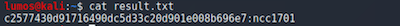
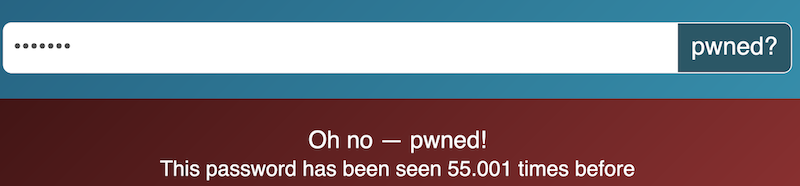
flag{55001}
OSINT

It was watering hole attack.
flag{watering hole}
Forensics
Amcaching In
I used Eric Zimmerman’s AmcacheParser tool.
https://ericzimmerman.github.io/ https://github.com/EricZimmerman/AmcacheParser
Give the hve file as input.
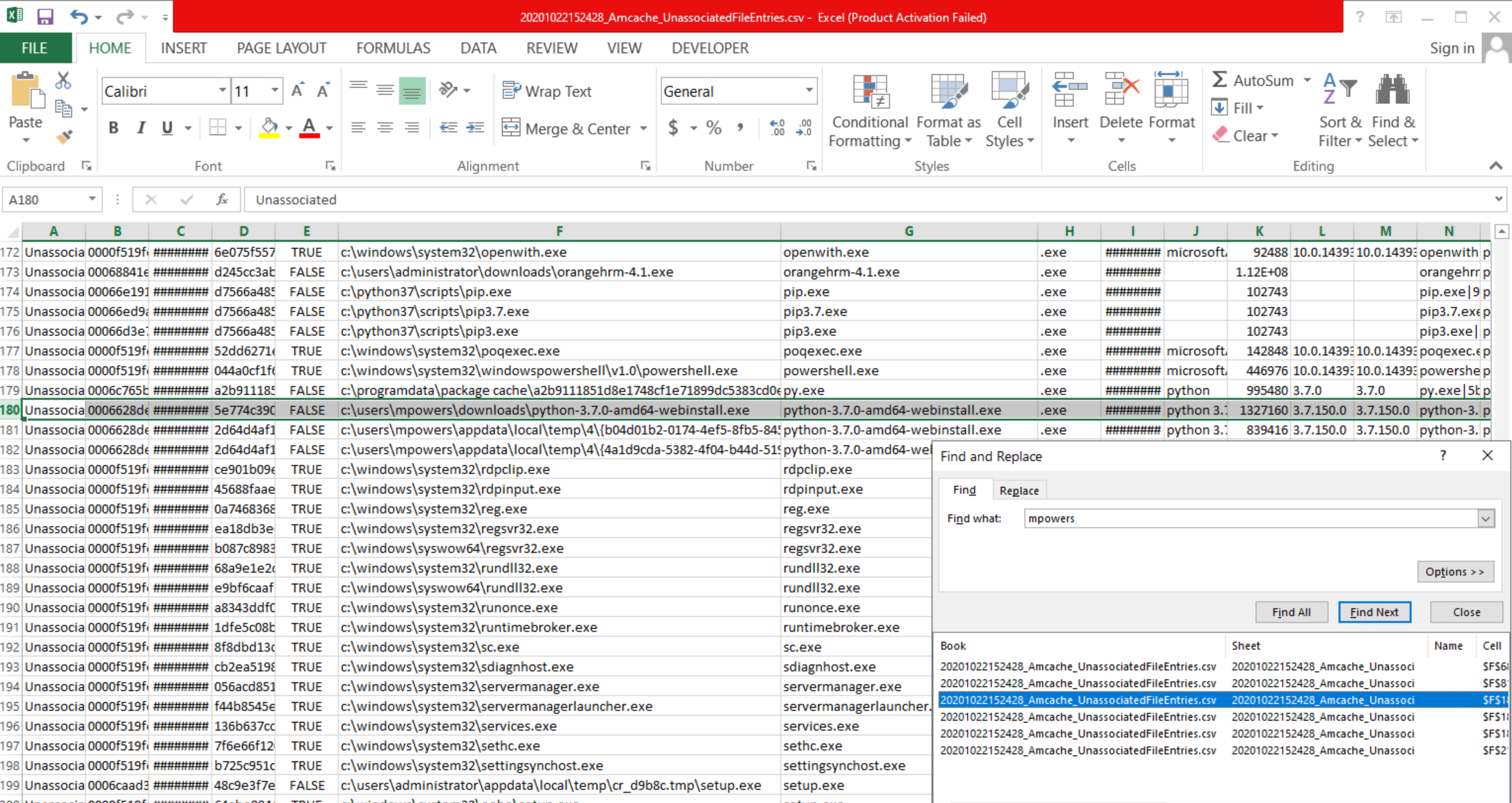
I searched “mpowers” in UnassociatedFileEntries.
We see that mpowers downloaded python-3.7.0-amd64-webinstall.exe. Flag is python.
flag{python}
Prefetch Perfection 2

There is another handy tool in Eris Zimmerman’s repo. PECmd (Prefetch Explorer Command Line)
https://github.com/EricZimmerman/PECmd
Execute command and we got 2 output file.
timestamp_PECmd_Output.csv timestamp_PECmd_Output_timeline.csv
Find “CMALDONADO\APPDATA\ROAMING\MICROSOFT\WINDOWS\COOKIES” in PECmd_Output.csv. There are three executable name, flag is DLLHOST.EXE.
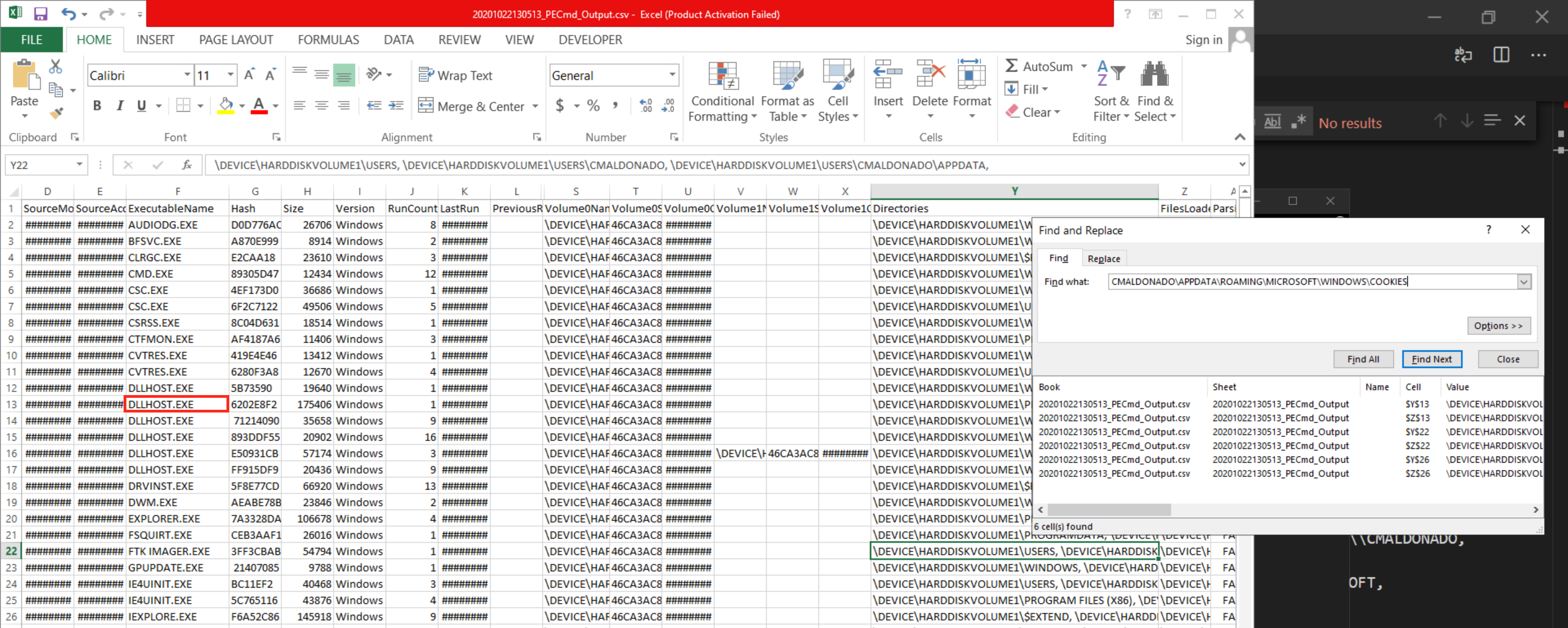
flag{dllhost.exe}
Traffic Analysis
Remotely Administrated Evil
We need to find executable file in given pcap file. There is GET request to /ot/solut.exe.
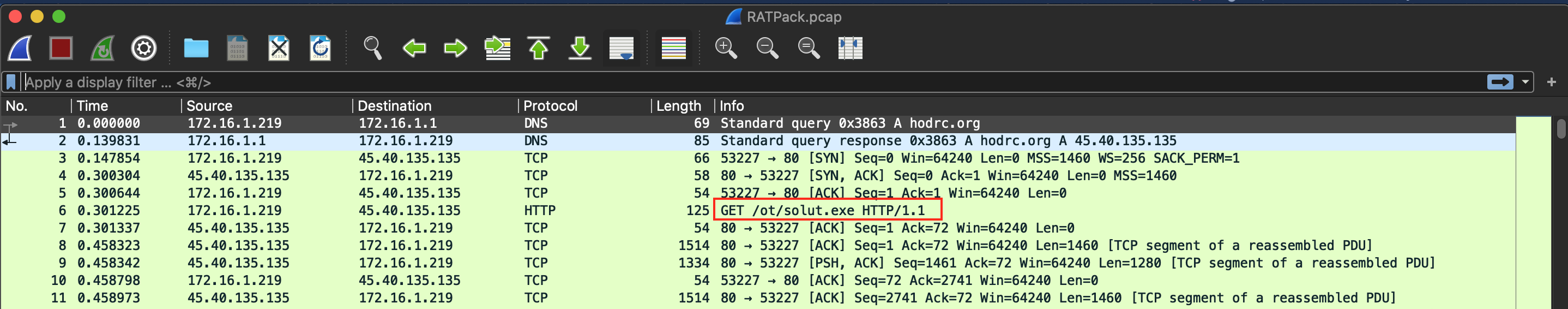
flag{solut.exe}
Remotely Administrated Evil 3
Search for “hodrc.org/ot/solut.exe rat” and find this site. “Netwire is an advanced RAT” this is the key line.
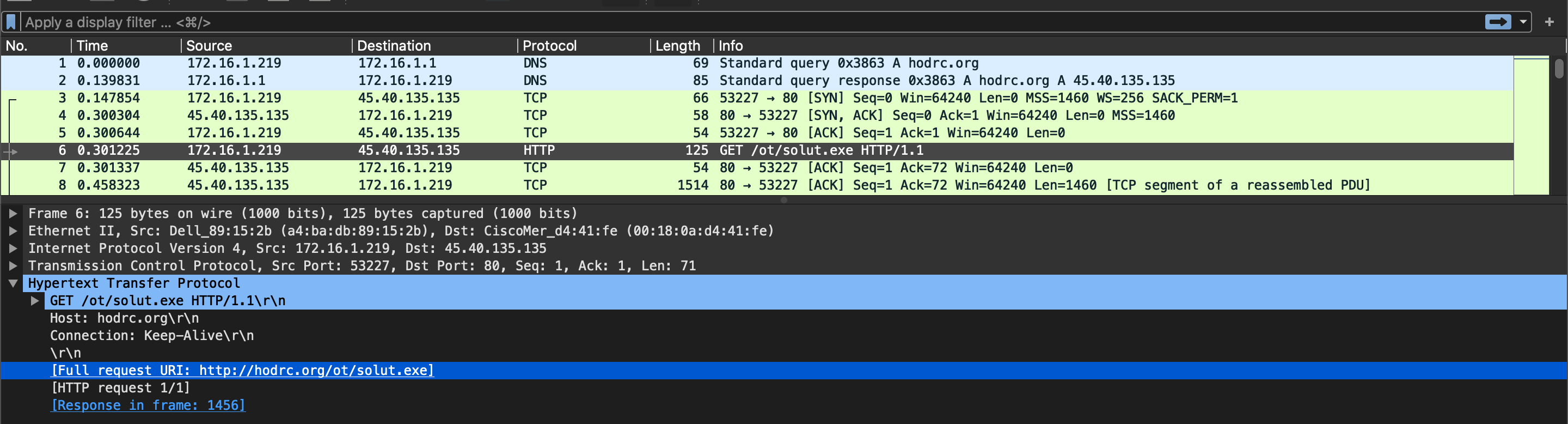
We can see our URL in Network activity.
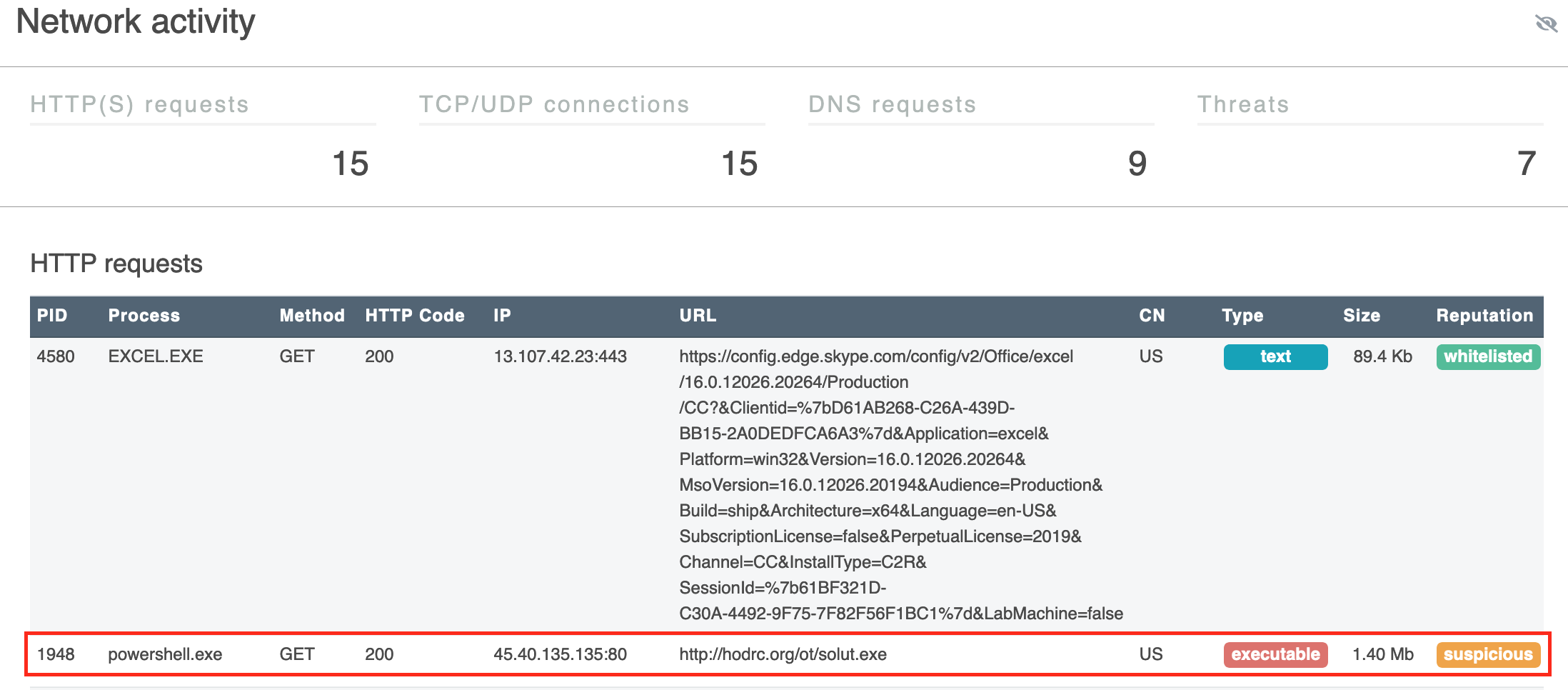
flag{netwire rat}
Evil Corp’s Child
We can see files URL in GET requsest. Download the file and get MD5 hash of it.
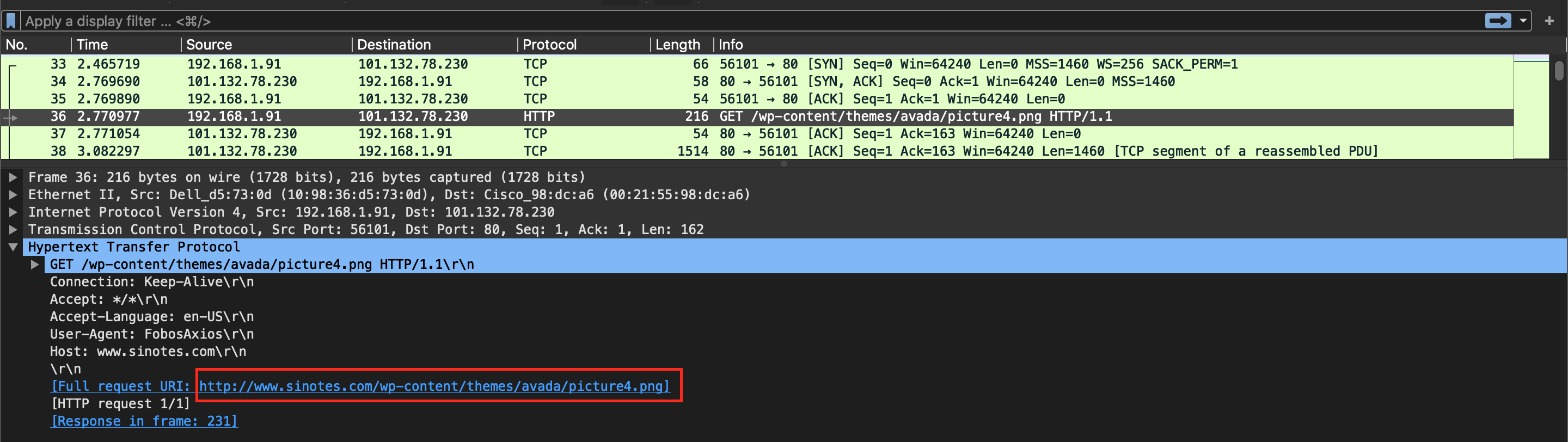
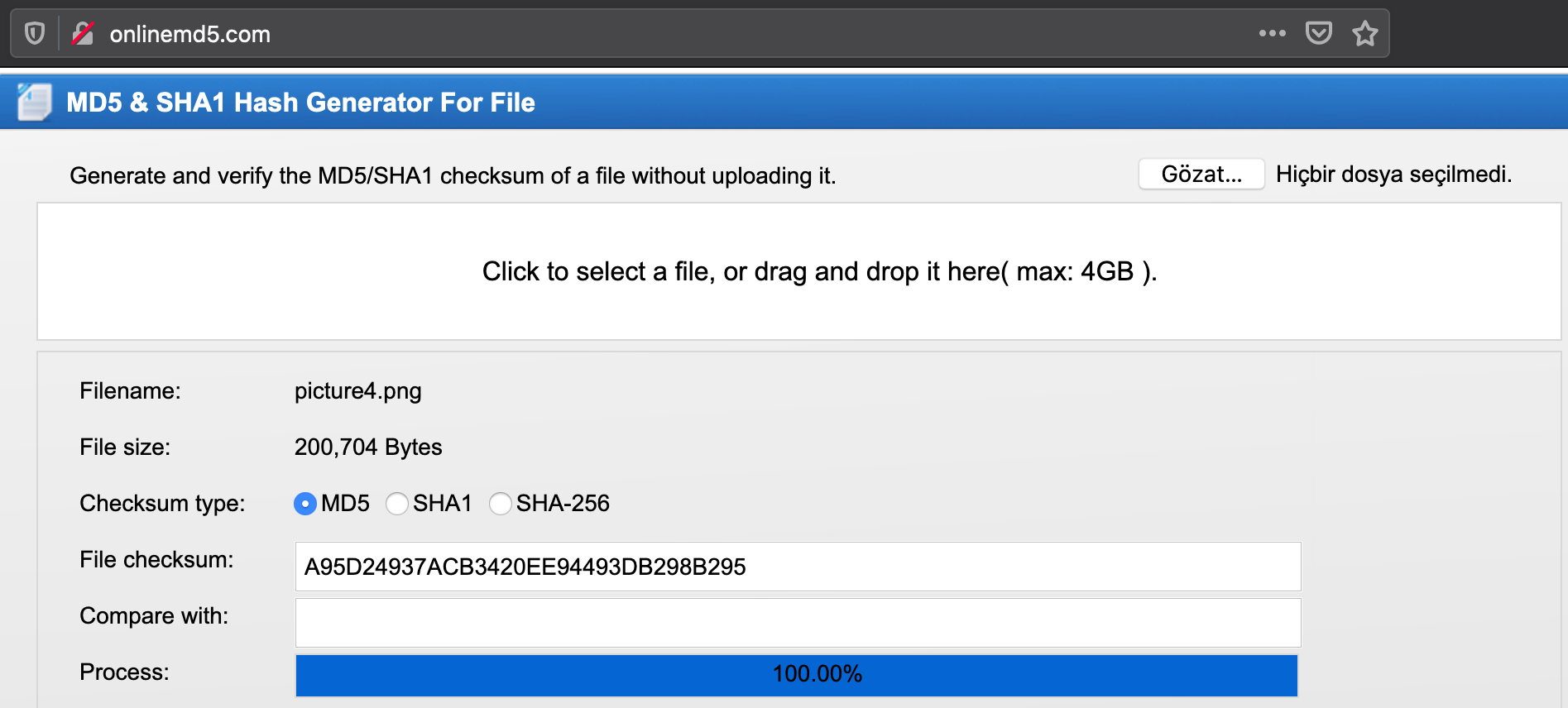
_ flag{a95d24937acb3420ee94493db298b295}_
Evil Corp’s Child 3
Filter ip.src == 37.205.9.252. Look https traffic start, Server Hello. In TLS there is localityname.
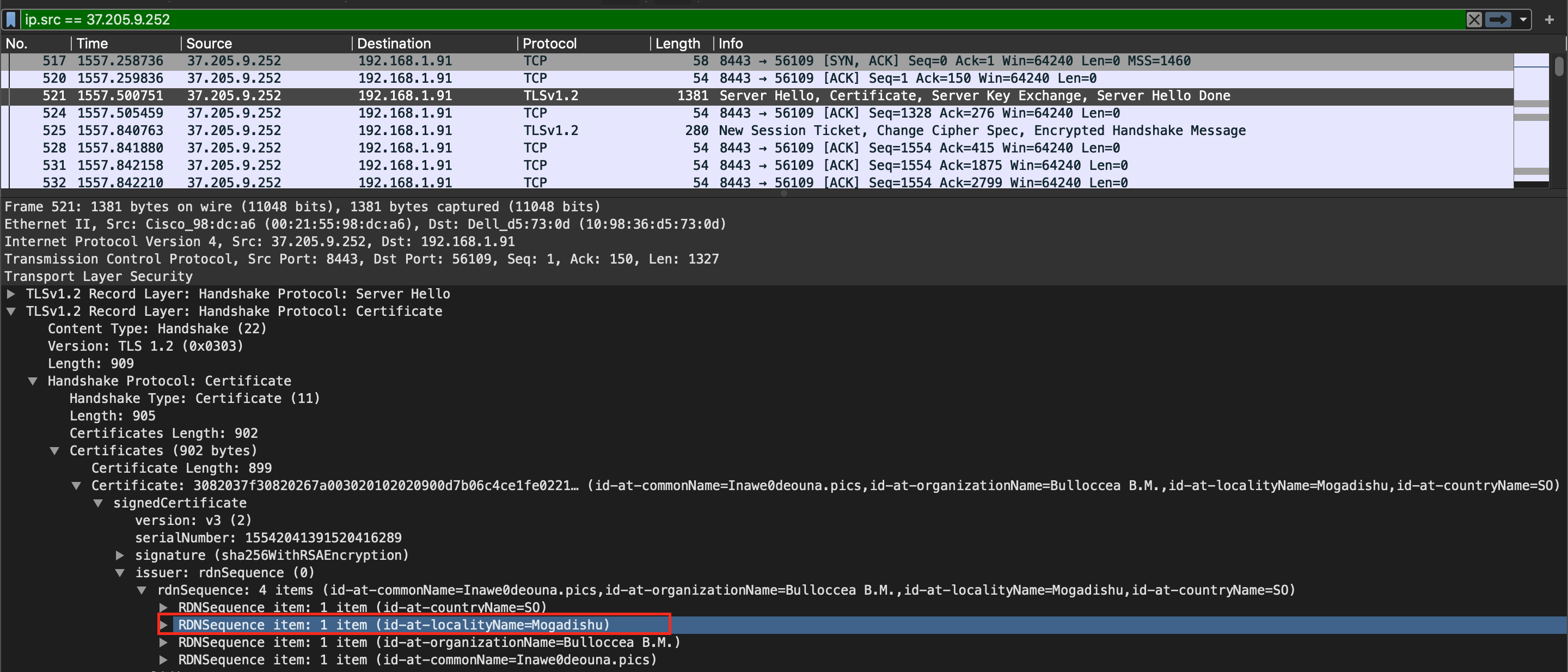
flag{Mogadishu}
Linux
Talking To The Dead 1
Connect with ssh to the server. Find for flag1.txt
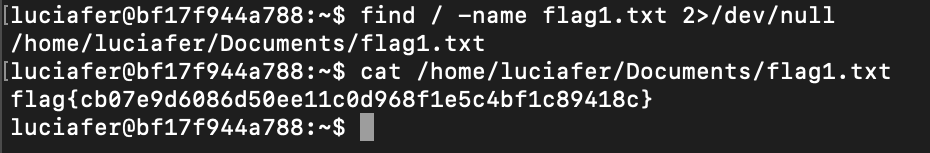
flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c}
Talking To The Dead 2
Use find command again but it didn’t find. Then I find for hidden files. Yes, there it is.
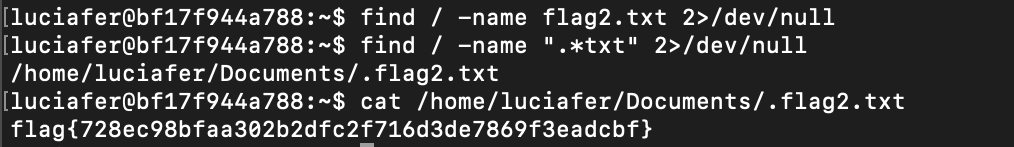
flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf}
Talking To The Dead 3
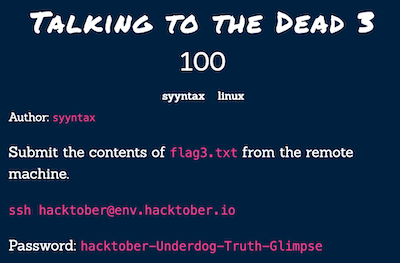
flag3.txt is in the spookyboi’s home directory. We need to switch user and use password that we find earlier as Past Demons flag. Then read it.
flag{445b987b5b80e445c3147314dbfa71acd79c2b67}
Talking To The Dead 4
flag4.txt is in root’s home directory. It says spookyboi doesn’t use root account. We can search for SUID files. There is /usr/local/bin/oujia. It reads the given file.
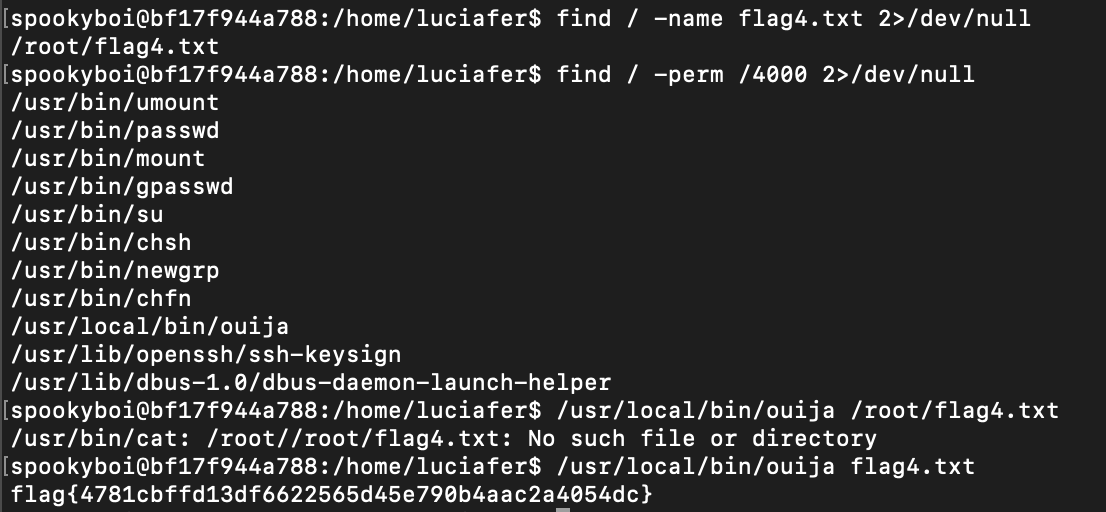
flag{4781cbffd13df6622565d45e790b4aac2a4054dc}